Flipper Zero : Tool or Menace?
The Flipper Zero may look like a toy, but it's a powerful hacking multi-tool, equipped with RFID, NFC, and Sub-GHz capabilities. Despite concerns about misuse, it's a favorite for security enthusiasts and pentesters.

At first glance, the beige and orange Flipper Zero might appear like a playful, Tamagotchi-style toy. However, beneath its unassuming exterior lies a powerful toolkit of hacking utilities. Equipped with everything from a Sub-GHz radio to an NFC reader, RFID tool, and IR blaster, the Flipper Zero sparked quite the commotion when it first hit the market in 2022. With its simple, accessible interface, this device has made testing digital security systems significantly more approachable. It has even garnered substantial media attention, and Amazon eventually banned its sale. But does the device live up to the hype?
What is a Flipper Zero?
The Flipper Zero was first introduced to the world in 2020 through a Kickstarter campaign that captured the imagination of tech enthusiasts, security professionals, and hobbyists alike. With an initial goal of just $60,000, the campaign surpassed all expectations, amassing an impressive $5 million in funding. This overwhelming success wasn’t just due to the device’s technical capabilities, but also because of its unique combination of accessibility and open-source design. Unlike many other security tools that require extensive technical knowledge, the Flipper Zero was designed to be user-friendly, appealing to beginners, while still offering powerful features for more advanced users.
At its core, the Flipper Zero is a multi-tool for pentesting (penetration testing), reverse engineering, and general hardware exploration. Its compact size, reminiscent of a retro handheld gaming device, and its approachable interface have made it popular not only with cybersecurity professionals but also with hobbyists curious about how everyday electronic systems work. The device runs on custom firmware, allowing users to interact with various protocols, such as RFID, NFC, Sub-GHz, and infrared, among others. Its open-source nature has fostered a thriving community, where users frequently share new modules, applications, and firmware updates, pushing the boundaries of what the Flipper can do.
The IR Blaster
Most modern remote control use infrared transmitters as they are simple and inexpensive to build. The Flipper is pre-programmed with most common protocols, allowing it control TVs, Projectors and Air Conditioners. Wether a particular device is supported is hit or miss. However, the Flipper can also record IR signal, allowing it to replace any remote you might own. For other remotes, there are large databases of IR signals that can be downloaded.
As a security tool, the Flipper can be used to determine how disruptive a malicious actor with a IR remote can be. A common example would be TV displays in stores and restaurants. Given that IR signals bounce around a room, it is fairly easy to record a signal from any remote used in the same room.
Around the house, the Flipper zero is a useful tool to replace a missing remote, or to play simple pranks. However, there is no lack of stories on Reddit on how the IR function can be used in public, often to mischievous result.
Sub-Ghz Radio
One of the standout features of the Flipper Zero is its ability to interact with devices operating on the Sub-GHz radio spectrum. Unlike infrared, which requires line-of-sight, Sub-GHz radio allows for communication over greater distances and without the need for direct visibility. This technology is commonly used in remote systems like garage door openers, car key fobs, and certain smart home devices. With the Flipper Zero, users can scan, analyze, and even emulate signals transmitted within this frequency range. This makes it an invaluable tool for testing the security of these wireless systems, as it can reveal whether a device is using outdated or insecure protocols.
However, not all older systems are easily exploitable. Even with unencrypted garage door openers, success in replicating signals can vary depending on factors like protocol variations or signal transmission strength. Modern systems, which use rolling codes or encryption, present an even greater challenge, as they are specifically designed to resist signal replication attempts.
RFID Tool
The Flipper Zero features a powerful RFID tool capable of reading, storing, and emulating low-frequency RFID tags, which are commonly used for access control in buildings, offices, and other secure areas. This functionality allows users to experiment with RFID technology by capturing and replicating signals from older or unencrypted systems. It also supports cloning these signals onto blank RFID cards or emulating them directly from the device, making it a versatile tool for testing and research.
In practice, this author successfully used to RFID tool to clone the key to the outdoor pool. By scanning the existing tag, storing its information, and emulating it with the Flipper, the author accessed the pool without needing the original key. This is only one example of the Flipper Zero interacting with primitive security systems.
NFC Reader
The Flipper Zero’s NFC functionality allows it to read and emulate high-frequency NFC tags, commonly found in contactless access systems, transit cards, and other wireless communication protocols. The device can scan, store, and emulate NFC signals, making it a versatile tool for exploring how these systems work. With its built-in NFC reader, users can capture the data from NFC-enabled devices and cards, and then emulate those signals, replicating the functionality of the original card or tag.
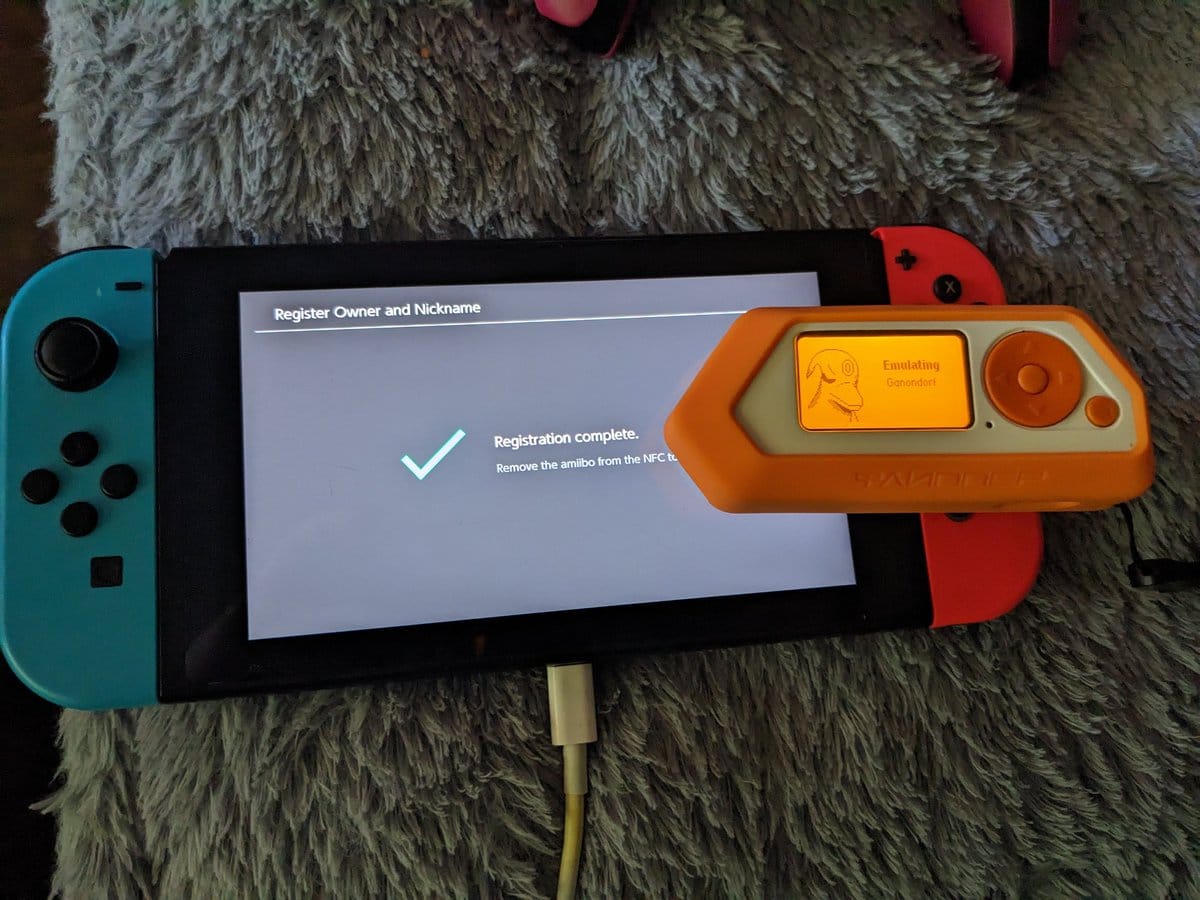
A unique application of the NFC emulation is its ability to interact with Amiibo toys. These figures, which store character data using NFC technology, can be scanned and emulated by the Flipper Zero. By reading the NFC tag embedded in the toy, the device can replicate the figure's data, allowing it to mimic the toys on compatible gaming platforms.
Bad USB
The Flipper Zero also includes a Bad USB feature, which allows it to emulate a USB Human Interface Device (HID) like a keyboard. When plugged into a computer, it can automatically execute predefined scripts that mimic keystrokes, enabling automated tasks or, in a more malicious context, injecting commands into a system without user consent. This functionality is commonly used in penetration testing to demonstrate how easily an attacker could exploit unsecured systems by running scripts to open terminals, download files, or modify system settings. While powerful for educational and testing purposes, the Bad USB feature highlights the importance of securing USB ports and monitoring connected devices to prevent potential misuse.
Endless Possibilities
The Flipper Zero stands out as a versatile, user-friendly tool that bridges the gap between hobbyist curiosity and professional security testing. Its broad range of functionalities opens up countless possibilities for exploring and testing the hidden signals and systems that surround us. While concerns about misuse have led to some restrictions on its sale, the device remains a valuable educational resource for understanding digital security and vulnerabilities. Whether for tinkering, pentesting, or creative projects, the Flipper Zero continues to captivate a wide audience, proving that powerful technology doesn’t always have to come in a complex package.